Protect Your Public Cloud Assets with
Cloud Security Assessment by Specialists
Make sure you are ready to move to the cloud, or have our experts look over the security of your current cloud deployments.
Talk to our Experts Today
INTRODUCTION
Experts from CybeNX will check and fix your cloud security
When using Public Cloud Infrastructure, cloud security review is a key part of setting security priorities. CyberNX’s Cloud Security Assessment services can help you make sure you are ready to move to the cloud or look at how your current cloud setup is working. Our cloud security assessments look at your cloud deployments to find holes in the design or configurations that could let hackers in. We then offer ways to fix these problems.
We address your key challenges:
When things are set up wrong in the cloud, security problems can happen, and businesses can face problems.
Your Cloud Service Provider (CSP) and industry norms should tell you what the best practices are for your cloud infrastructure.
Regulatory bodies like RBI, SEBI, or IRDA have rules that cloud technology must follow.
Companies need to make sure that their cloud security governance practices are in line with their security strategy.
Set up good cloud security monitoring to find security risks right away and take action.
Set up and launch important cloud components safely, such as containers, virtual machines (VMs), storage buckets, and load balancers.
To make sure that cloud operation is safe, organizations must have the right skills and knowledge in cloud security management.
PROCESS
How It Works?
Looking for Cloud Security Assessment Services? Connect with us.
APPROACH
Why should you choose CyberNX to Check the Security of the Cloud?
Cutting-Edge Tools
Client-Centric Approach
Risk Mitigation
Actionable Insight
Regulatory Compliance
Customer first Approach is our guiding principle.
BENEFITS
Get Clear Picture of Your Cloud's Safety and Compliance
Highly Specialised Professionals
Our team of cloud security experts has experience protecting a wide range of cloud environments in many different businesses.
Comprehensive Security Evaluation
To find vulnerabilities, we carefully look at configurations, access controls, network design, and data storage.
Technical Insights and Recommendations
We give you technical information that you can use and personalized suggestions, such as changes to the setup, better access control, encryption, and ways to reduce threats.
Enhanced Incident Response Preparedness
We help you make your incident reaction plans stronger, cut down on the time it takes to respond, and keep the impact of incidents on operations to a minimum.
Documentation and Reporting
For stakeholders, IT teams, and auditors, we give thorough reports that summarize findings, suggestions, and steps to fix problems.
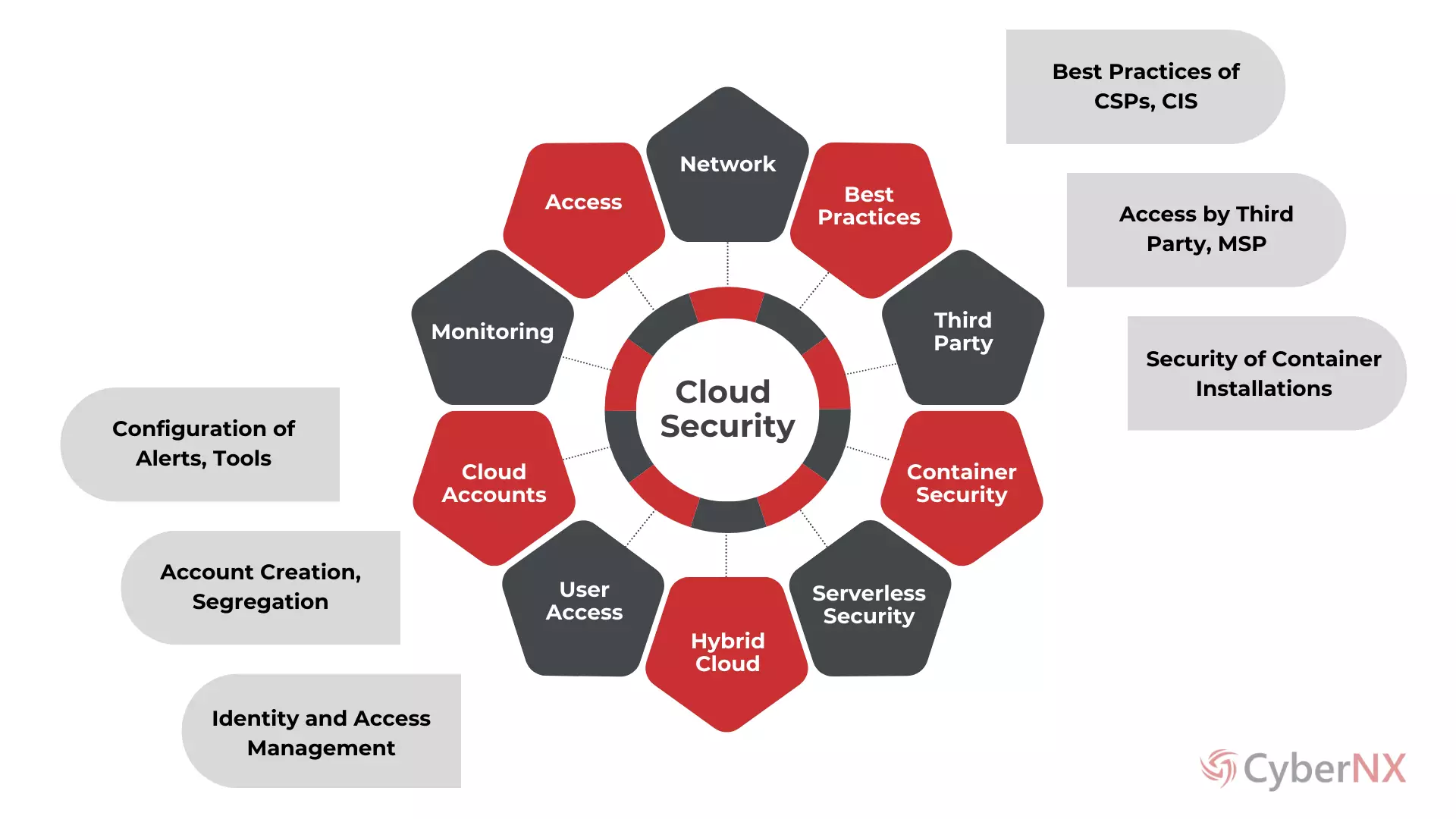
ASSESSMENT AREAS
Cloud Security Assessment Areas
Cloud Security Assessment |
Description |
Access Controls |
Evaluation of user authentication, authorization mechanisms, and access privileges to ensure only authorized individuals can access resources. |
Network Security |
Analysis of network architecture, segmentation, firewalls, and intrusion detection systems to prevent unauthorized access and data exfiltration. |
Data Encryption |
Assessment of data encryption methods and key management practices to protect data at rest and in transit from unauthorized access. |
Identity and Access Management |
Review of identity lifecycle management, multi-factor authentication, and role-based access control to ensure proper user identity verification and access control. |
Configuration Management |
Examination of cloud service configurations to ensure adherence to security best practices and mitigate misconfiguration risks. |
Logging and Monitoring |
Evaluation of logging mechanisms, event monitoring, and anomaly detection systems to detect and respond to security incidents promptly. |
Incident Response |
Assessment of incident response plans, procedures, and team readiness to effectively mitigate and recover from security breaches. |
Compliance and Regulatory Requirements |
Verification of compliance with industry regulations and standards such as RBI, SEBI, IRDA, GDPR, PCI DSS, and adherence to organizational policies. |
Threat Detection and Prevention |
Implementation of threat intelligence feeds, malware scanning, and security analytics to identify and mitigate security threats in real-time. |
Security Training and Awareness |
Review of employee security awareness training programs to educate staff on security best practices and mitigate human-related security risks. |
Disaster Recovery and Business Continuity |
Evaluation of backup and recovery processes, redundancy measures, and continuity plans to ensure data resilience and business continuity in the event of disasters. |
Vendor Risk Management |
Assessment of third-party vendor security practices and contracts to mitigate risks associated with outsourcing cloud services. |
For Customized Plans tailored to Your Needs,
Get in Touch Today!
FAQ
Frequently Asked Questions
RESOURCES

