
SEBI CSCRF Deadline Extended. Secure Your Organization NOW!
The Securities and Exchange Board of India (SEBI) has recently provided much-needed relief to Regulated Entities (REs) by extending the
Contents
In today’s interconnected world, cyber threats are more sophisticated and persistent than ever. A single vulnerability can expose your organization to devastating consequences. This is where Vulnerability Assessment and Penetration Testing (VAPT) becomes indispensable.
This guide provides a comprehensive overview of VAPT in Cyber Security, its significance in protecting your digital assets, and how to find the best Vulnerability Assessment and Penetration Testing Service provider to strengthen your security posture.
VAPT combines Vulnerability Assessment (VA) and Penetration Testing (PT). VA identifies weaknesses in your IT infrastructure. PT simulates real-world attacks to exploit those weaknesses. Together, they provide a holistic view of your security posture.
VAPT is crucial for protecting your business in today’s threat landscape. It offers numerous benefits:
Just as businesses vary in size and industry, so do their IT infrastructures and security needs. That’s why this services are often tailored to specific areas of your technology landscape and the level of access granted to the testers.
Let’s explore both the types of VAPT and the common testing methodologies used:
Within each of the VAPT types described above, different testing methodologies often called “box” testing can be employed, depending on the desired level of access and knowledge of the testers:
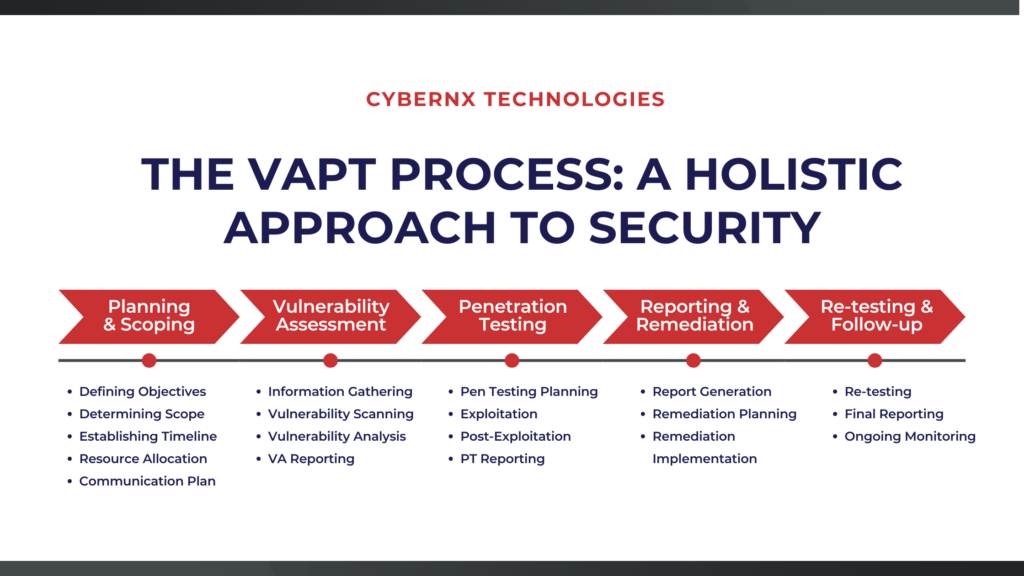
Here’s a breakdown of the typical VAPT process:
This crucial initial phase sets the stage for the entire VAPT engagement. It involves defining objectives, scope, timeline, and resources.
This phase focuses on identifying and documenting potential security weaknesses:
This phase simulates real-world attacks to test the exploitability of identified vulnerabilities:
This phase focuses on communicating the findings and addressing the identified vulnerabilities. It combines VA and PT reports to generate comprehensive VAPT reports. Remediation planning and implementation are done in this phase to mitigate the identified vulnerabilities.
This final phase verifies the effectiveness of the remediation efforts by verifying fixes, generating final report, and implementing ongoing monitoring.
Many industry regulations and standards (e.g., ISO 27001, PCI DSS, HIPAA, SOC 2) require regular VAPT audits. These audits provide independent verification of your security posture and demonstrate due diligence to regulators, customers, and partners. This audit involves a thorough review of your security controls, vulnerability assessments, penetration testing results, and remediation efforts. It helps identify gaps in your security program and ensures you are meeting compliance requirements.
Beyond compliance, a VAPT audit can also provide valuable insights into your overall security effectiveness and identify areas for improvement. A well-conducted audit can give you confidence in your security posture and help you prioritize future security investments.
Effective VAPT services are built on a foundation of key principles, ensuring thoroughness, value, and alignment with your business needs. Understanding these principles helps you evaluate the quality of VAPT services offered and make informed decisions about your security investments.
Vulnerability Assessment and Penetration Testing relies on specialized software tools to automate and enhance the assessment process. These vulnerability testing tools empower security professionals to work efficiently and effectively.
VAPT tools can be broadly categorized based on their primary function:
The choice of VAPT tools depends on the specific needs of the assessment, such as target systems, budget, expertise, and reporting capabilities.
While vulnerability testing tools are essential, they are not a substitute for human expertise. Skill and experience of the security tester truly makes this testing effective.
VAPT security professionals are needed to:
Vulnerability Assessment and Penetration Testing is an investment in your business’s security, and like any investment, it’s important to understand the costs involved and the return you can expect.
The cost of VAPT services in India can vary significantly depending on several factors:
While VAPT involves a cost, the return on investment can be substantial, primarily through the prevention of costly security incidents.
Here are some key areas where this service delivers ROI:
Vulnerability Assessment and Penetration Testing is not just an expense; it’s an investment in your business’s security and future. By understanding the costs and the potential return, you can make informed decisions about your security investments and protect your organization from the potentially devastating consequences of a cyberattack.
While all organizations benefit from VAPT, certain sectors face amplified cyber risks due to the sensitive data they handle, critical infrastructure they manage, or stringent regulatory requirements.
Here are some key industries where VAPT is particularly vital:
Selecting the right Vulnerability Assessment and Penetration Testing service provider is crucial for ensuring the security of your business. A thorough engagement minimizes your cyber risk, while a poorly executed one can leave you vulnerable. Here’s what to consider:
In today’s dynamic threat landscape, Vulnerability Assessment and Penetration Testing is an essential component of any robust security strategy. By partnering with a trusted VAPT services in India like CyberNX Technologies, you can proactively identify and address vulnerabilities, minimize your risk exposure, and strengthen your overall security posture.
Ready to strengthen your security posture? Schedule a free consultation with our VAPT experts today!
How do I know if my business needs VAPT testing?
Ans: If your business uses any IT systems, applications, or networks, you need VAPT testing. It’s essential for identifying vulnerabilities that could be exploited by attackers.
How do VAPT tests fit into my overall security strategy?
Ans: VAPT tests are a crucial part of a proactive security strategy. They provide valuable insights into your security posture, allowing you to prioritize remediation efforts and reduce your risk of cyberattacks.
How long does a typical VAPT assessment take?
Ans: The duration of a VAPT assessment varies depending on the scope and complexity of the target systems. A typical assessment can take anywhere from a few days to several weeks.
How often should I conduct VAPT testing?
Ans: Regular VAPT testing is crucial. The frequency depends on your risk profile and industry regulations. At a minimum, annual testing is recommended, with more frequent assessments for critical systems or after significant changes to your infrastructure.
What results can I expect after the VAPT test is completed?
Ans: You can expect a detailed report outlining the identified vulnerabilities, their severity, and recommendations for remediation. This report will help you prioritize your security efforts and address the most critical weaknesses.
Who should conduct VAPT testing?
Ans: VAPT testing should be conducted by qualified security professionals. You can use internal teams, external security firms, or a combination of both. Cert-In empaneled providers like CyberNX Technologies offer specialized expertise.
How does VAPT help with regulatory compliance?
Ans: Many regulations require organizations to conduct regular security assessments. VAPT helps you meet these requirements by providing documented evidence of your security testing efforts.
Is VAPT testing legal and ethical?
Ans: Yes, VAPT testing is both legal and ethical when performed with proper authorization. It’s crucial to obtain explicit permission from the system owner before conducting any penetration testing activities. Cert-In empaneled providers like CyberNX Technologies follow strict ethical guidelines and legal regulations.
Share on
RESOURCES

The Securities and Exchange Board of India (SEBI) has recently provided much-needed relief to Regulated Entities (REs) by extending the

Cyberattacks are a constant threat. But what if you could fight fire with fire? Penetration testing methodologies are the tools

In the fast-paced world of cybersecurity, staying ahead of evolving threats requires more than just reactive measures. CISOs, CXOs, and
RESOURCES
Cyber Security Knowledge Hub
Copyright © 2025 CyberNX | All Rights Reserved | Terms and Conditions | Privacy Policy