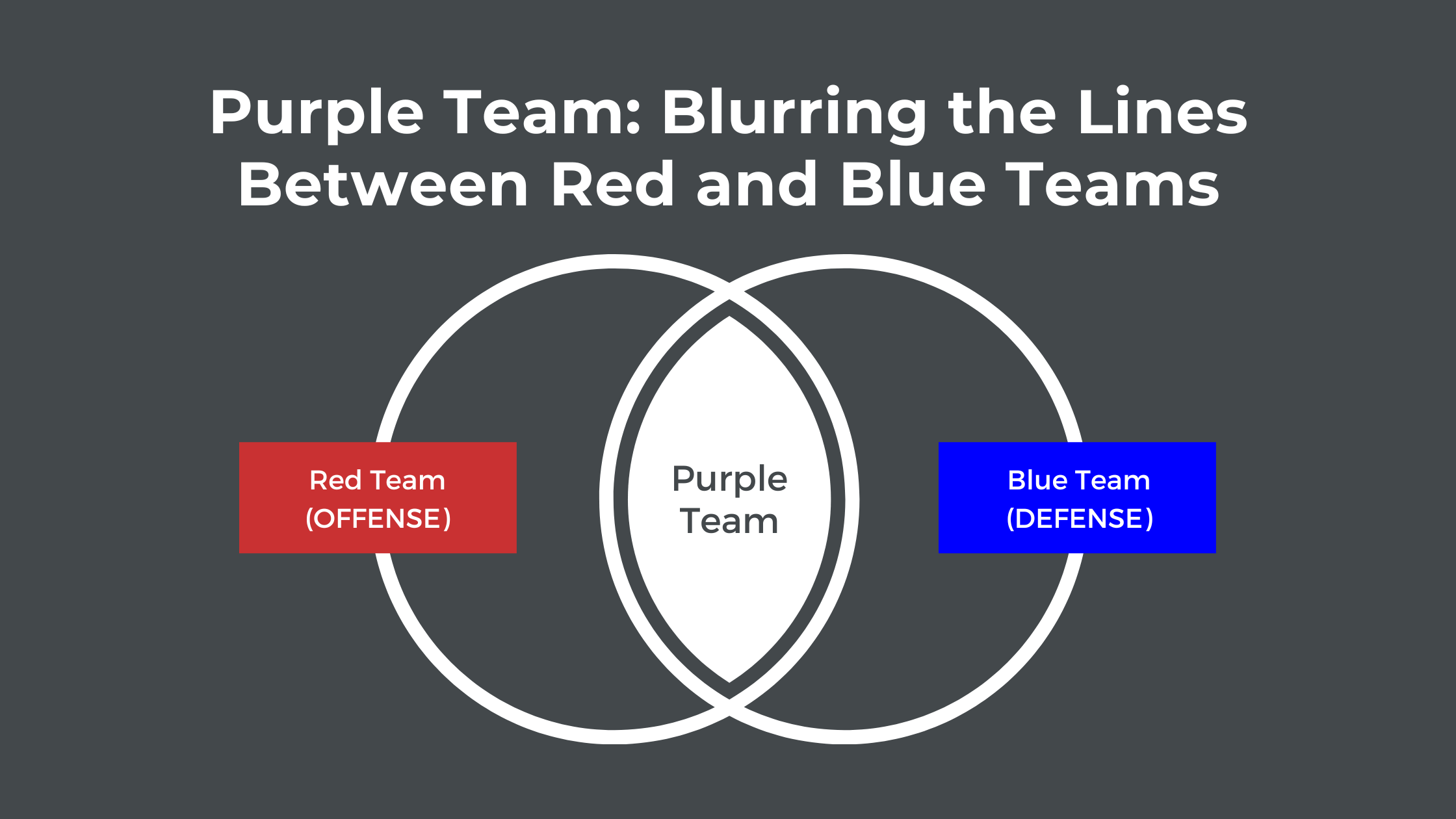
Purple Team Cybersecurity: Enhance Security with Real-Time Collaboration
In the ever-evolving landscape of cybersecurity, CISOs, CXOs, and IT Managers are constantly seeking innovative strategies to fortify their defenses.
Contents
Cybersecurity has changed. It’s no longer enough to simply react to attacks; you need to anticipate them. Breach attack simulation tools (BAS Tools) represent a fundamental shift in cybersecurity strategy, moving from reactive defense to proactive offense. Our blog dives into the best BAS tools for 2025, helping you embrace this proactive approach and build a more resilient security posture.
Breach attack simulation tools (BAS tools) are game-changers in modern cybersecurity. They allow you to simulate real-world cyberattacks on your own systems, identifying vulnerabilities before hackers do. Think of it as a cybersecurity fire drill. BAS tools create realistic attack scenarios, from phishing emails to ransomware attacks, and assess how your existing security controls would perform. This proactive approach is essential for staying ahead of the curve in today’s dynamic threat landscape.
The cyber threat landscape is constantly evolving. Attackers are using increasingly sophisticated techniques, from AI-powered malware to complex social engineering tactics. Traditional security measures, like firewalls and antivirus software, are no longer enough. In 2025, BAS tools are critical because they:
Choosing the right breach simulation tool is essential. Here are some key features to consider:
For a more detailed breakdown of essential criteria, be sure to check out our guide on the Top 10 Criteria for Choosing the Right Breach Attack Simulation Tools.
Here’s a look at some of the top breach attack simulation tools available in 2025:
Let’s elaborate on these Breach Attack Simulation tool (BAS tool) descriptions, providing more detail and context:
Choosing the right breach attack simulation tool is a critical decision. By carefully evaluating your needs and considering the factors outlined in this guide, you can select a solution that will help you proactively strengthen your defenses and stay ahead of the evolving cyber threat landscape. Remember, the best tool is the one that best fits your specific requirements and budget.
Choosing the right BAS tool can be complex. Our team of cybersecurity experts can help you assess your needs and select the best solution for your organization. Contact us today for a free consultation.
Share on
RESOURCES

In the ever-evolving landscape of cybersecurity, CISOs, CXOs, and IT Managers are constantly seeking innovative strategies to fortify their defenses.
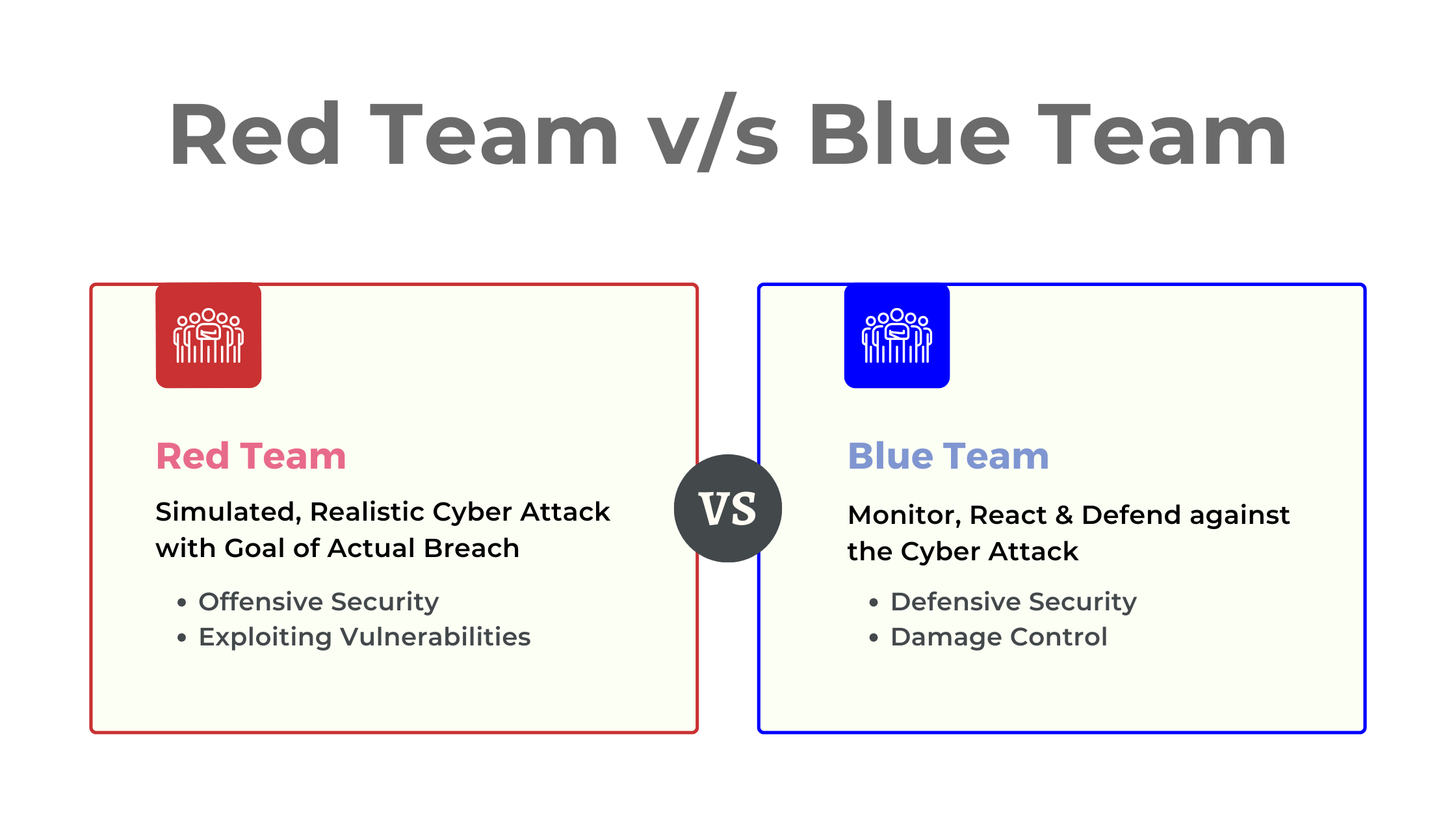
In the relentless battle against cyber threats, CISOs, CXOs, and IT Managers are constantly seeking ways to fortify their organization’s

Cybersecurity is a continuous battle, not a one-time fix. In today’s complex digital world, threats are constantly evolving, becoming more
RESOURCES
Cyber Security Knowledge Hub