An IBM report revealed that the global average cost of data breach crossed approximately 5 million in 2024. With cyberattack cases increasing exponentially, numbers are set to jump in 2025 and beyond.
Today, businesses are operating in an interconnected world where cyber threats are sophisticated and persistent than ever. The primary goal of cybercriminals is to steal sensitive data or disrupt operations. A single known vulnerability here or there is usually the cause, leading to devastating consequences. This is where Vulnerability Assessment and Penetration Testing (VAPT) become indispensable. It protects data and helps you meet compliance needs set by regulatory bodies too.
Our VAPT guide provides a comprehensive overview of this cybersecurity practice, its significance in protecting your digital assets, and how to find the best VAPT Service provider to strengthen your security posture.
What is Vulnerability Assessment and Penetration?
VAPT combines Vulnerability Assessment (VA) and Penetration Testing (PT). Vulnerability assessment helps in identifying and exposing vulnerabilities in the targeted systems. This exercise is usually carried out using automation tools. The findings are shared with the security teams.
Penetration Testing acts upon the vulnerability assessment findings. In this exercise, pentesters exploit those weaknesses found and see how far a hacker can go deep into your system.
Together, they provide a holistic view of your security posture.
Why is VAPT Important for Your Business?
VAPT auditors impersonate real-life cybercriminals and understand how they could exploit vulnerabilities in your systems, websites or apps. Once testing is completed, they share report flagging vulnerabilities and share mitigation strategies. This plays a crucial role in protecting your business in today’s threat landscape.
It offers numerous other benefits:
- Proactive Security: Identify and address vulnerabilities before attackers exploit them, minimizing breach risks.
- Risk Mitigation: Understand your vulnerabilities to prioritize remediation and allocate resources effectively.
- Compliance: Meet regulatory requirements and industry standards (e.g., ISO 27001, PCI DSS).
- Cost-Effectiveness: Investing in this service is far more cost-effective than recovering from a security incident.
- Strengthened Security Posture: Enhance your overall security, reducing downtime and disruptions.
- Reputation Protection: Safeguard your company’s reputation by proactively managing security risks.
- Competitive Advantage: Demonstrate a strong security posture to stakeholders and customers, building trust and confidence.
VAPT Types & Methodologies
Just as businesses vary in size and industry, so do their IT infrastructures and security needs. That’s why this services are often tailored to specific areas of your technology landscape and the level of access granted to the testers.
Let’s explore both the types of VAPT and the common testing methodologies used:
Types of Vulnerability Assessment and Penetration Testing
- Wireless Network VAPT: Identifies vulnerabilities in wireless networks and associated devices (routers, firewalls, switches).
- Web Application VAPT: Assesses web application security, focusing on vulnerabilities like SQL injection and cross-site scripting (XSS).
- Mobile Application VAPT: Evaluates mobile app security across different operating systems.
- API VAPT: Focuses on the security of Application Programming Interfaces (APIs).
- Cloud VAPT: Examines the security of cloud infrastructure and applications.
- Social Engineering VAPT: Assesses human vulnerabilities through simulated phishing, pretexting, and other social engineering attacks.
VAPT Methodologies: How to Approach the Testing?
Within each of the VAPT types described above, different testing methodologies often called “box” testing can be employed, depending on the desired level of access and knowledge of the testers:
- Black Box Testing: Simulates an external attack. Testers have no prior knowledge of the target system’s internals.
- White Box Testing: Testers have full knowledge of the target system, including source code, diagrams, and configurations.
- Gray Box Testing: A hybrid approach. Testers have partial system knowledge, balancing external and internal perspectives.
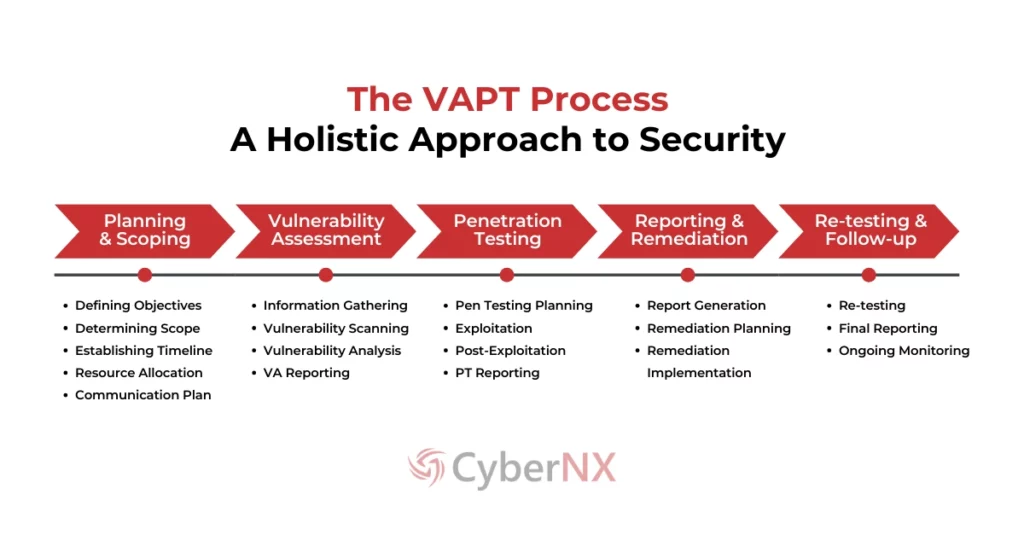
The VAPT Process: A Holistic Approach to Security
Vulnerability assessment and Penetration testing provides a comprehensive approach to identifying and mitigating security risks. It combines the proactive identification of vulnerabilities (VA) with the simulated exploitation of those vulnerabilities (PT) to provide a holistic view of an organization’s security posture.
Here’s a breakdown of the typical VAPT process:
Phase 1: Planning and Scoping
This crucial initial phase sets the stage for the entire VAPT engagement. It involves defining objectives, scope, timeline, and resources.
Phase 2: Vulnerability Assessment (VA)
This phase focuses on identifying and documenting potential security weaknesses:
- Information Gathering: Collecting data about the target systems, including network architecture, software versions, and configurations.
- Vulnerability Scanning: Using automated tools to scan the target systems for known vulnerabilities.
- Vulnerability Analysis: Analyzing the results of the vulnerability scan to identify and prioritize the most critical vulnerabilities.
- VA Reporting: Generating a report that documents all identified vulnerabilities, their severity levels, and recommended remediation steps.
Phase 3: Penetration Testing (PT)
This phase simulates real-world attacks to test the exploitability of identified vulnerabilities:
- Penetration Testing Planning: Defining the scope and objectives of the penetration test, based on the findings of the vulnerability assessment.
- Exploitation: Attempting to exploit the identified vulnerabilities in a controlled environment to demonstrate the potential impact of a successful attack.
- Post-Exploitation: Assessing what an attacker could achieve after gaining access to a system, such as escalating privileges, moving laterally within the network, or exfiltrating data.
- PT Reporting: Generating a detailed report that documents the exploited vulnerabilities, the potential impact of the attacks, and recommended remediation steps.
To understand the step-by-step process, check out our detailed guide on the phases of penetration testing
Phase 4: Reporting and Remediation
This phase focuses on communicating the findings and addressing the identified vulnerabilities. It combines VA and PT reports to generate comprehensive Vulnerability Assessment and Penetration Testing reports. Remediation planning and implementation are done in this phase to mitigate the identified vulnerabilities.
Phase 5: Re-testing and Follow-up
This final phase verifies the effectiveness of the remediation efforts by verifying fixes, generating final report, and implementing ongoing monitoring.
VAPT Audits: Ensuring Compliance and Strengthening Security
Many industry regulations and standards (e.g., ISO 27001, PCI DSS, HIPAA, SOC 2) require regular VAPT audits. These audits provide independent verification of your security posture and demonstrate due diligence to regulators, customers, and partners. A Vulnerability Assessment and Penetration Testing audit involves a thorough review of your security controls, vulnerability assessments, penetration testing results, and remediation efforts. It helps identify gaps in your security program and ensures you are meeting compliance requirements.
Beyond compliance, a VAPT audit can also provide valuable insights into your overall security effectiveness and identify areas for improvement. A well-conducted audit can give you confidence in your security posture and help you prioritize future security investments.
Guiding Principles of Effective VAPT Services
Effective VAPT services are built on a foundation of key principles, ensuring thoroughness, value, and alignment with your business needs. Understanding these principles helps you evaluate the quality of Vulnerability Assessment and Penetration Testing services offered and make informed decisions about your security investments.
- Comprehensive Coverage: Covers all relevant aspects of your IT infrastructure – networks, applications (web, mobile, APIs), cloud environments, and other critical systems.
- Risk-Based Approach: Prioritizes the identification and remediation of the most critical vulnerabilities.
- Non-Disruptive Testing: Testing during off-peak hours or using techniques that minimize the impact on live systems.
- Continuous Testing: Taking care of new vulnerabilities and attack techniques emerging regularly.
- Confidentiality: Maintains strict confidentiality and protects your data from unauthorized access or disclosure.
What are VAPT Tools and Why Are They Essential?
Vulnerability Assessment and Penetration Testing relies on specialized VAPT software tools to automate and enhance the assessment process. These vulnerability testing tools empower security professionals to work efficiently and effectively.
Categories of VAPT Tools
Vulnerability Assessment and Penetration Testing tools can be broadly categorized based on their primary function:
- Vulnerability Scanners: These tools automate the process of identifying known vulnerabilities in systems, applications, and networks. They compare the target’s configuration against databases of known weaknesses. Examples include Nessus, OpenVAS, and QualysGuard.
- Penetration Testing Frameworks: These provide a platform for conducting penetration tests, offering tools for information gathering, exploitation, post-exploitation, and reporting. Metasploit is a widely used example.
- Web Application Security Scanners: These tools specialize in identifying vulnerabilities in web applications, such as SQL injection, cross-site scripting, and authentication bypasses. Burp Suite, OWASP ZAP, and Acunetix are popular choices.
- Network Analysis Tools: These tools help analyze network traffic, identify suspicious activity, and understand how attackers might try to infiltrate a network. Wireshark is a prominent example.
- Fuzzers: Fuzzers send malformed or unexpected input to applications to identify potential crashes or vulnerabilities.
The choice of VAPT tools depends on the specific needs of the assessment, such as target systems, budget, expertise, and reporting capabilities.
The Importance of VAPT Expertise
While Vulnerability Assessment and Penetration Testing tools are essential, they are not a substitute for human expertise. Skill and experience of the security tester truly makes VAPT effective.
VAPT security professionals are needed to:
- Configure the tools correctly.
- Interpret the results.
- Prioritize vulnerabilities.
- Develop effective remediation strategies.
The Cost of VAPT and Its Return on Investment
Vulnerability Assessment and Penetration Testing is an investment in your business’s security, and like any investment, it’s important to understand the costs involved and the return you can expect.
Factors Affecting VAPT Costs
The cost of Vulnerability Assessment and Penetration Testing services can vary significantly depending on several factors:
- Scope & Type of Testing: Broader the scope, higher the cost and vice versa.
- Size and Complexity of Infrastructure: Larger and more complex IT infrastructure require more time and effort to assess, leading to higher costs.
- Expertise of the Provider: Highly experienced and certified VAPT providers (e.g.CERT-IN Empanlled VAPT Vendor) typically charge more than less experienced ones.
- Reporting and Deliverables: More comprehensive reporting may require more time and effort from the provider.
- Frequency of Testing: Regular, recurring VAPT engagements may have a different pricing structure than one-time assessments.
Return on Investment (ROI) of VAPT
While VAPT involves a cost, the return on investment can be substantial, primarily through the prevention of costly security incidents.
Here are some key areas where Vulnerability Assessment and Penetration Testing deliver ROI:
- Preventing Data Breaches: This testing significantly reduces the risk of a data breach, saving your business potentially millions of dollars.
- Compliance Savings: Many industry regulations and compliance standards (e.g., PCI DSS, HIPAA, ISO 27001) require regular VAPT.
- Enhanced Security Posture: This testing strengthens your overall security posture, making your organization a less attractive target for cybercriminals.
- Protecting Brand Reputation: This helps protect your brand by proactively identifying and mitigating vulnerabilities that could lead to such incidents.
Vulnerability Assessment and Penetration Testing is not just an expense; it’s an investment in your business’s security and future. By understanding the costs and the potential return, you can make informed decisions about your security investments and protect your organization from the potentially devastating consequences of a cyberattack.
VAPT: Protecting Vulnerable Industries from Cyber Threats
While all organizations benefit from VAPT, certain sectors face amplified cyber risks due to the sensitive data they handle, critical infrastructure they manage, or stringent regulatory requirements.
Here are some key industries where Vulnerability Assessment and Penetration Testing is particularly vital:
- Financial Services: Protecting vast amounts of sensitive financial data is paramount. This service is essential for preventing fraud, securing customer data, and maintaining regulatory compliance (e.g., PCI DSS).
- Healthcare: Safeguarding highly sensitive patient data is critical. This testing helps protect patient privacy, ensures data integrity, and maintains HIPAA compliance.
- Government and Public Sector: Protecting citizen data and critical infrastructure is a national security imperative. This testing is crucial for preventing cyberattacks that could disrupt essential services or compromise sensitive information.
- E-commerce and Retail: Securing customer data, including credit card information, is essential for online retailers. VAPT helps prevent data breaches, minimizes financial losses, and maintains PCI DSS compliance.
- Technology and IT: Protecting valuable intellectual property and sensitive customer data is crucial for technology companies. VAPT helps prevent cyber espionage, data theft, and maintains a competitive edge.
- Manufacturing and Industrial: Securing complex systems and industrial control systems (ICS) is vital. This testing helps prevent disruptions, ensures operational continuity, and mitigates safety risks.
- Energy and Utilities: Protecting critical infrastructure is paramount. VAPT helps prevent cyberattacks that could disrupt essential services, destabilize the grid, or cause widespread outages.
- Education: Safeguarding student and faculty data is essential. VAPT helps protect privacy, ensures data security, and maintains compliance with regulations like FERPA.
- Telecommunications: Securing vast networks and protecting customer data is crucial. VAPT helps prevent data breaches, ensures network security, and maintains service availability.
- Legal: Protecting highly confidential client information is a legal and ethical imperative. VAPT helps maintain client confidentiality, ensures data integrity, and upholds professional standards.
Choosing the Right VAPT Partner: Key Considerations
Selecting the right Vulnerability Assessment and Penetration Testing service provider is crucial for ensuring the security of your business. A thorough engagement minimizes your cyber risk, while a poorly executed one can leave you vulnerable. Here’s what to consider:
- Certifications and Accreditations: Look for recognized certifications (CREST, OSCP, CEH, CISSP, GIAC) and accreditations (e.g. CERT-In). These validate expertise and adherence to standards.
- Experience and Expertise: Inquire about their experience with organizations like yours. Ask for case studies and client references. Ensure they have specialists in areas relevant to your needs.
- Methodology and Tools: A well-defined methodology is essential. Ask about their process and the tools they use. They should leverage both commercial and open-source solutions for comprehensive coverage.
- Clear Reporting: Clear, concise, and actionable reporting is vital. Request sample reports to assess their quality.
- Scope and Customization: The provider should tailor their services to your specific needs, budget, risk tolerance, and objectives.
- Cost and Value: Don’t focus solely on price. A cheaper option might be less thorough. Focus on the value you receive. Get transparent pricing upfront.
- Post-Engagement Support: Inquire about their support for remediation planning, implementation, and re-testing. This is crucial for closing the loop on identified vulnerabilities.
In today’s dynamic threat landscape, Vulnerability Assessment and Penetration Testing is an essential component of any robust security strategy. By partnering with a trusted VAPT provider like CyberNX Technologies, you can proactively identify and address vulnerabilities, minimize your risk exposure, and strengthen your overall security posture.
Ready to strengthen your security posture? Schedule a free consultation with our VAPT experts today!
FAQS
How do I know if my business needs VAPT testing?
If your business uses any IT systems, applications, or networks, you need VAPT testing. It’s essential for identifying vulnerabilities that could be exploited by attackers.
How do VAPT tests fit into my overall security strategy?
VAPT tests are a crucial part of a proactive security strategy. They provide valuable insights into your security posture, allowing you to prioritize remediation efforts and reduce your risk of cyberattacks.
How long does a typical VAPT assessment take?
The duration of a VAPT assessment varies depending on the scope and complexity of the target systems. A typical assessment can take anywhere from a few days to several weeks.
How often should I conduct VAPT testing?
Regular VAPT testing is crucial. The frequency depends on your risk profile and industry regulations. At a minimum, annual testing is recommended, with more frequent assessments for critical systems or after significant changes to your infrastructure.
What results can I expect after the VAPT test is completed?
You can expect a detailed report outlining the identified vulnerabilities, their severity, and recommendations for remediation. This report will help you prioritize your security efforts and address the most critical weaknesses.
Who should conduct VAPT testing?
VAPT testing should be conducted by qualified security professionals. You can use internal teams, external security firms, or a combination of both. Cert-In empaneled providers like CyberNX Technologies offer specialized expertise.
How does VAPT help with regulatory compliance?
Many regulations require organizations to conduct regular security assessments. VAPT helps you meet these requirements by providing documented evidence of your security testing efforts.
Is VAPT testing legal and ethical?
Yes, VAPT testing is both legal and ethical when performed with proper authorization. It’s crucial to obtain explicit permission from the system owner before conducting any penetration testing activities. Cert-In empaneled providers like CyberNX Technologies follow strict ethical guidelines and legal regulations.