The enterprise cloud revolution is already here. As of 2024, over 90% of enterprises use some form of cloud service with 67% of infrastructure now fully cloud based.
It’s like businesses are building in the bright shining sky by leveraging AWS, Azure and Google Cloud to host applications, store data and scale operations faster than ever. But those in the know recognise the dark and gloom too – which is that with cloud adoption comes an expanded threat landscape. The recent cyberattack on Indian startup KiranaPro is the case in point.
Attackers are now slipping through misconfigured buckets, compromised API gateways and overlooked IAM policies faster than one can think. Such are cloud environments – dynamic, ephemeral, and distributed, making them a beloved playground for persistent threat actors.
Cloud-based penetration testing thus becomes more than a best practice. It should be seen as a business imperative. Find out more!
Understanding Cloud Penetration Testing
Imagine cloud penetration testing as a stress test on the cloud environment composed of APIs, storage points, VMs, containers and access policies to find weak points.
Unlike traditional pentesting, cloud pentesting is about navigating layered permissions, invisible perimeters and orchestrated services that scale and change in real-time.
It mimics attackers while respecting the shared responsibility model of cloud service providers, unveiling many benefits for security teams.
Want to know about other types of Penetration Testing? Check our blog: Types of Penetration Testing: A Complete Overview.
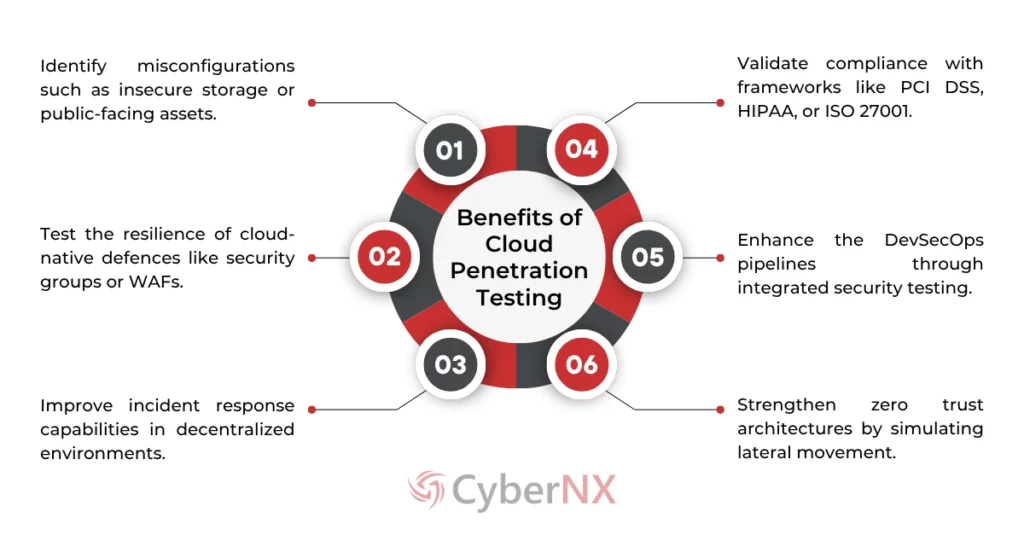
Be Aware of Cloud Penetration Testing Benefits
Cloud penetration testing goes beyond surface-level security checks – it helps uncover hidden risks, validate defences, and strengthen compliance across complex cloud infrastructures. By understanding its benefits, businesses can build safer, more resilient, and regulation-ready cloud environments.
1. Expose Hidden Cloud Weaknesses
Cloud pentesting helps organizations uncover critical misconfigurations, insecure data storage, and exposed public-facing assets that attackers often exploit. By testing the resilience of cloud-native defences such as firewalls, WAFs, and security groups, cloud pentesting ensures your infrastructure is hardened against evolving cyber threats.
2. Ensure Compliance and Operational Readiness
Through comprehensive cloud pentesting, businesses can validate compliance with leading standards like PCI DSS, HIPAA, and ISO 27001. It also enhances incident response capabilities by identifying how your teams and systems perform under simulated attack conditions across multi-cloud or hybrid environments.
3. Build Secure, Future-Ready Cloud Systems
Cloud pentesting seamlessly integrates into DevSecOps pipelines, helping security and development teams address vulnerabilities earlier in the lifecycle. It also reinforces zero trust architectures by simulating real-world lateral movement and privilege escalation attempts—ensuring your cloud environment remains secure, scalable, and resilient.
Methodology: Know How Penetration Testing Works in Cloud Environments
Cloud based penetration testing methodologies are customised to the subtleties of the cloud.
1. Reconnaissance
Identify exposed services such as public S3 buckets and cloud assets. Enumeration of subdomains, certificates and metadata endpoints occurs at this phase.
2. Cloud Configuration Review
Review IAM policies, security groups, VPC configurations and logging setups. Identify overly permissive roles or unprotected access controls.
3. Access Control Testing
Attempt to exploit weak identity configurations are made. This includes privilege escalation from service roles to administrator roles or misuse of permissions like iam:PassRole or s3:GetObject.
4. Service Exploitation
Test serverless functions, unprotected APIs, container configurations and cloud resource endpoints for vulnerabilities and misconfigurations.
5. Post-Exploitation
Simulate lateral movement within the environment, data access or even manipulation of resources such as RDS snapshots or ECS clusters.
6. Reporting and Remediation Guidance
All findings are documented with detailed proof-of-concept, risk levels, business impact and remediation strategies tailored for cloud services.
Types and Methods of Cloud Penetration Testing
Cloud pentesting encompasses a range of approaches, from external and internal assessments to API and configuration testing, tailored to your cloud environment. These methods help identify vulnerabilities, test defences, and ensure robust security across all cloud layers.
1. Based on Testing Approach
Here, we lay out three different approaches that can be used for cloud based penetration testing.
- Black Box Testing Simulates an external attacker with no prior access. The focus is on discovering externally exposed resources and misconfigurations without insider knowledge.
- White Box Testing The tester is provided with full access to system configurations, architectural diagrams and credentials. This approach is thorough and ideal for validating deep security controls and internal permissions.
- Grey Box Testing Combines aspects of both black and white box testing. The tester has limited access, simulating insider threats or persistent attackers with partial knowledge of the environment.
2. Based on Cloud Provider Environment
AWS and Azure – they are well-known cloud providers. Knowing how penetration testing is done on these platforms can help in making better decisions.
- AWS Cloud Penetration Testing Tools such as Prowler and Pacu are used to assess IAM policies, S3 permissions, EC2 metadata exposure and Lambda privileges. It is important to know that AWS allows pentesting within defined parameters as per their policy.
- Azure Cloud Penetration Testing Tools like Azucar and MicroBurst target services such as Azure AD, Key Vault, App Services and Logic Apps. Emphasis is placed on RBAC roles, storage access and automation workflows.
Cloud vs. Traditional Penetration Testing
Cloud based penetration testing is quite different from other pentesting services because of the shared responsibility model.
In traditional environments, the organization manages everything from hardware to applications. In the cloud, the provider is responsible for the security of the infrastructure while customers are responsible for the configuration and usage of services.
Here’s how cloud pentesting differs when compared to traditional pentesting:
- In AWS, the organization cannot test the physical hypervisor or network layer, but it can assess its own IAM policies, access logs and service configurations.
- Cloud pentesting requires a deep understanding of cloud-native tools and permission models, unlike traditional pentesting which focuses on known perimeter weaknesses.
- Authorization is another crucial component in cloud pentesting. Each cloud service provider has an Acceptable Use Policy that governs what can and cannot be tested. Failing to comply could lead to service disruption or legal action.
Common Threats Found in Cloud Based Penetration Testing
Cloud environments face a unique blend of security challenges that stem from misconfigurations, poor access controls, and the dynamic nature of multi-tenant infrastructure. These threats can expose sensitive data, disrupt services, and create entry points for attackers if not addressed proactively through rigorous testing and continuous monitoring.
Scope of a Cloud Penetration Test
1. Define Ownership Boundaries
Establish what cloud resources are within the organization’s control. This clarifies legal and operational boundaries for testing.
2. Asset Classification
Identify production versus staging environments, sensitive versus public assets, and which resources are transient or persistent.
3. Cloud Models
Determine whether the test will include Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), or Software-as-a-Service (SaaS) components.
4. Include CI/CD Pipelines
Testing the deployment pipeline ensures code, secrets, and permissions are secure throughout the development lifecycle.
5. Third-Party Integrations
OAuth, SSO, and external connectors should be tested for over-permissioned access and integration flaws.
Testing Methodologies and Tools Used
Cloud penetration testing aligns with industry standards such as the OWASP Cloud-Native Application Security Top 10, MITRE ATT&CK for Cloud and NIST SP 800-53/800-115.
These frameworks guide the testing of configurations, identities and service-level vulnerabilities. Tools like Pacu (AWS exploitation), ScoutSuite (cloud auditing), Prowler (AWS compliance), and Azucar (Azure assessment) are commonly used.
CIS Benchmarks for AWS, Azure and GCP ensure baseline security, while CREST and OSSTMM offer structured methodologies.
Testing is also shaped by each cloud provider’s acceptable use policies and security guidelines to ensure compliance and prevent service disruption.
Conclusion
Cloud environments, no doubt, offer agility, scalability and cost-efficiency. But they also introduce evolving threats. A trusted and experienced cloud penetration testing team is essential for proactive defence. CyberNX is one such cybersecurity firm offering cloud based penetration testing. Talk to our experts today to know more about our certifications, capabilities and outcomes delivered to clients.
Cloud Penetration Testing FAQs
Who should consider cloud penetration testing?
Any organization using cloud services, especially those handling sensitive data, operating in regulated industries (like finance or healthcare), or deploying public-facing apps should invest in cloud penetration testing. Startups scaling rapidly, enterprises moving to multi-cloud environments, or teams practicing DevOps and continuous delivery also greatly benefit from regular cloud security assessments.
Is permission required to perform cloud pentests?
Yes. Major cloud providers like AWS, Azure, and GCP have specific policies that define what you can and cannot test. You must follow their guidelines, submit testing requests if needed, and obtain explicit written approval to avoid violating terms of service or triggering automated defences.
How often should cloud penetration testing be performed?
Ideally, it should be conducted at least annually and after major changes such as new deployments, cloud migrations or configuration updates. Frequent testing is also recommended when scaling infrastructure, adopting new services, or integrating third-party tools that impact cloud security.
What are the most common issues found in cloud pentests?
Frequent findings include misconfigured storage buckets, excessive IAM permissions, exposed APIs, lack of logging, and insecure serverless functions. Other issues include unpatched containers, overly permissive firewall rules, and inadequate monitoring of user and system activity.