Advanced Digital Forensic Services
Request a Free Demo
INTRODUCTION
CyberNX - Your Trusted Digital Forensics Services Partner

We address your key challenges:
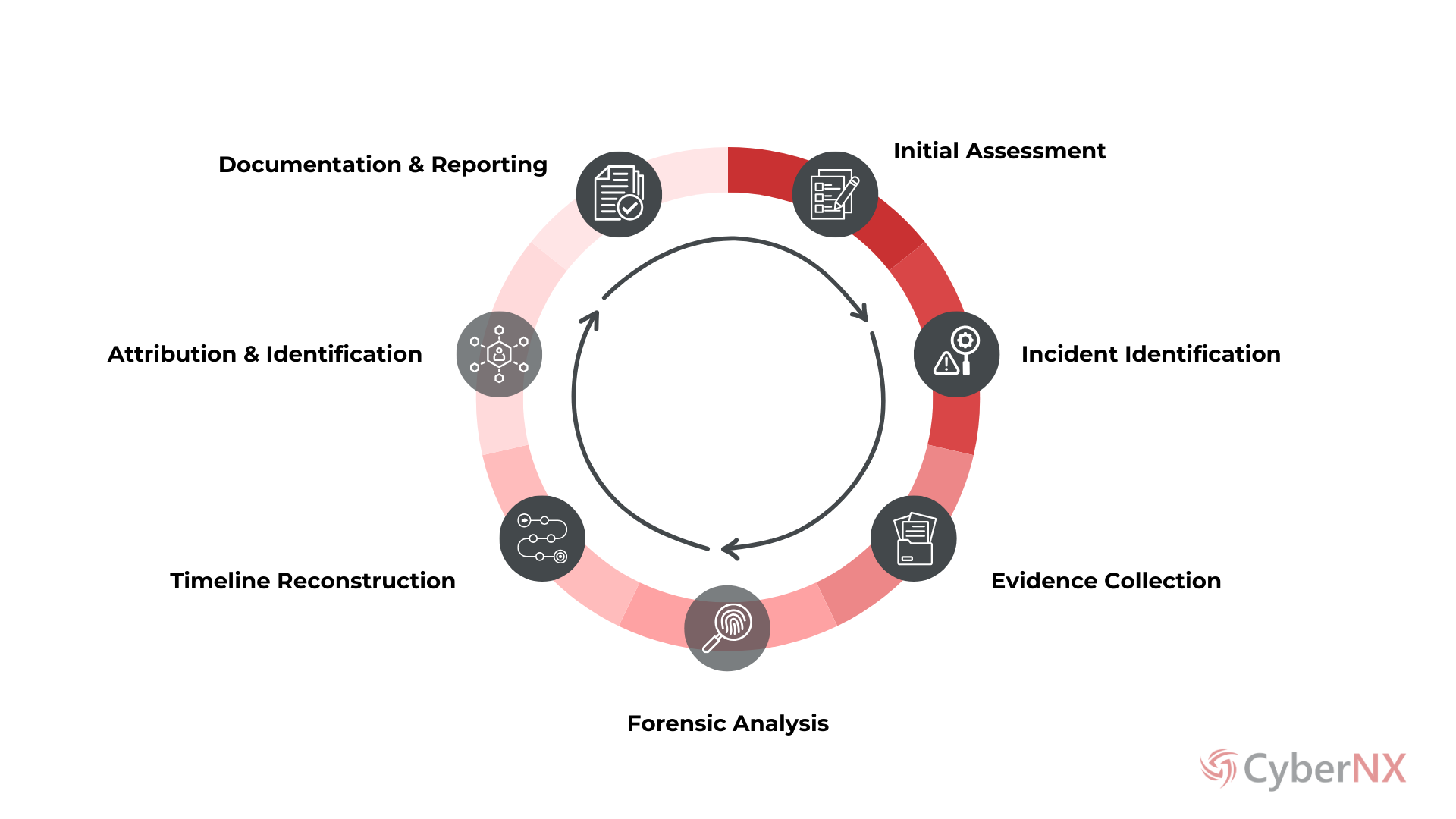
How It Works?
APPROACH
Digital Forensic Services - Why Choose CyberNX?
01
Initial Assessment
02
Incident Identification
03
Evidence Collection
04
Forensic Analysis
05
Attribution and Identification
06
Documentation and Reporting
Looking for Digital Forensics Services? Connect with Our Cybersecurity Experts!
BENEFITS
Comprehensive Forensics Services by CyberNX
Expert Team
Our professionals are highly experienced in digital forensics, ensuring thorough and precise investigations.
Cutting-Edge Technology
We utilize the latest tools and technologies to deliver top-tier forensic services.
Confidentiality and Integrity
We maintain the highest standards of confidentiality and integrity, ensuring your privacy throughout our investigations.
Customized Solutions
Each case is unique; we tailor our services to meet your specific needs, providing targeted and effective solutions.
24/7 Emergency Response
Cyber threats can occur at any time. Our team is available around the clock to respond swiftly to any digital incident.
Customer first Approach is our guiding principle.
PLANS
Key Areas in Forensic Services
Forensic Service |
Cloud Forensics |
Host Forensics |
Network Forensics |
Mobile Forensics |
Definition |
Investigation of digital evidence on cloud platforms such as AWS, Azure, or Google Cloud. |
Examination of digital evidence on individual computers or devices like laptops, desktops, or servers. |
Analysis of digital evidence transmitted over networks, including traffic logs, packet captures, and network devices. |
Examination of digital evidence on mobile devices such as smartphones or tablets. |
Scope |
Focuses on data stored, accessed, or transmitted through cloud services. |
Concentrates on data stored locally on devices or accessed by those devices. |
Centers on data transmitted over networks, including internal and external communication. |
Concentrates on data stored, accessed, or transmitted through mobile devices' operating systems and applications. |
Tools Used |
Tools specialized for cloud service providers' environments. |
Tools for disk imaging, memory analysis, and file system examination. |
Tools like Wireshark, tcpdump, or Snort for capturing and analyzing network traffic. |
Tools like UFED, mobile device imaging and data extraction. |
Common Use Cases |
Investigating data breaches, unauthorized access, or insider threats in cloud environments. |
Incident response, malware analysis, and recovering deleted files from individual devices. |
Identifying network intrusions, detecting unauthorized access, or analyzing suspicious traffic patterns. |
Digital forensics in criminal investigations, employee misconduct, or data theft cases involving mobile devices. |
For Customized Plans tailored to Your Needs,
Get in Touch Today!
RESOURCES
Cyber Security Knowledge Hub
FAQ
