Test your Cyber Defence Capabilities with
Breach Attack Simulation (BAS) Services
Simulate real-world cyberattacks to identify vulnerabilities and assess security controls, strengthening organizational defenses.
Talk to our Experts Today





















INTRODUCTION
CyberNX - Your Breach Attack Simulation Exercise Partner
CyberNX helps businesses find and stop security threats by providing Breach Attack Simulation (BAS) services. In a controlled setting, our BAS drills act out cyberattacks like malware and phishing to find weak spots and test defenses. We help you with everything, from planning to fixing problems, so your business is ready for real-world risks.
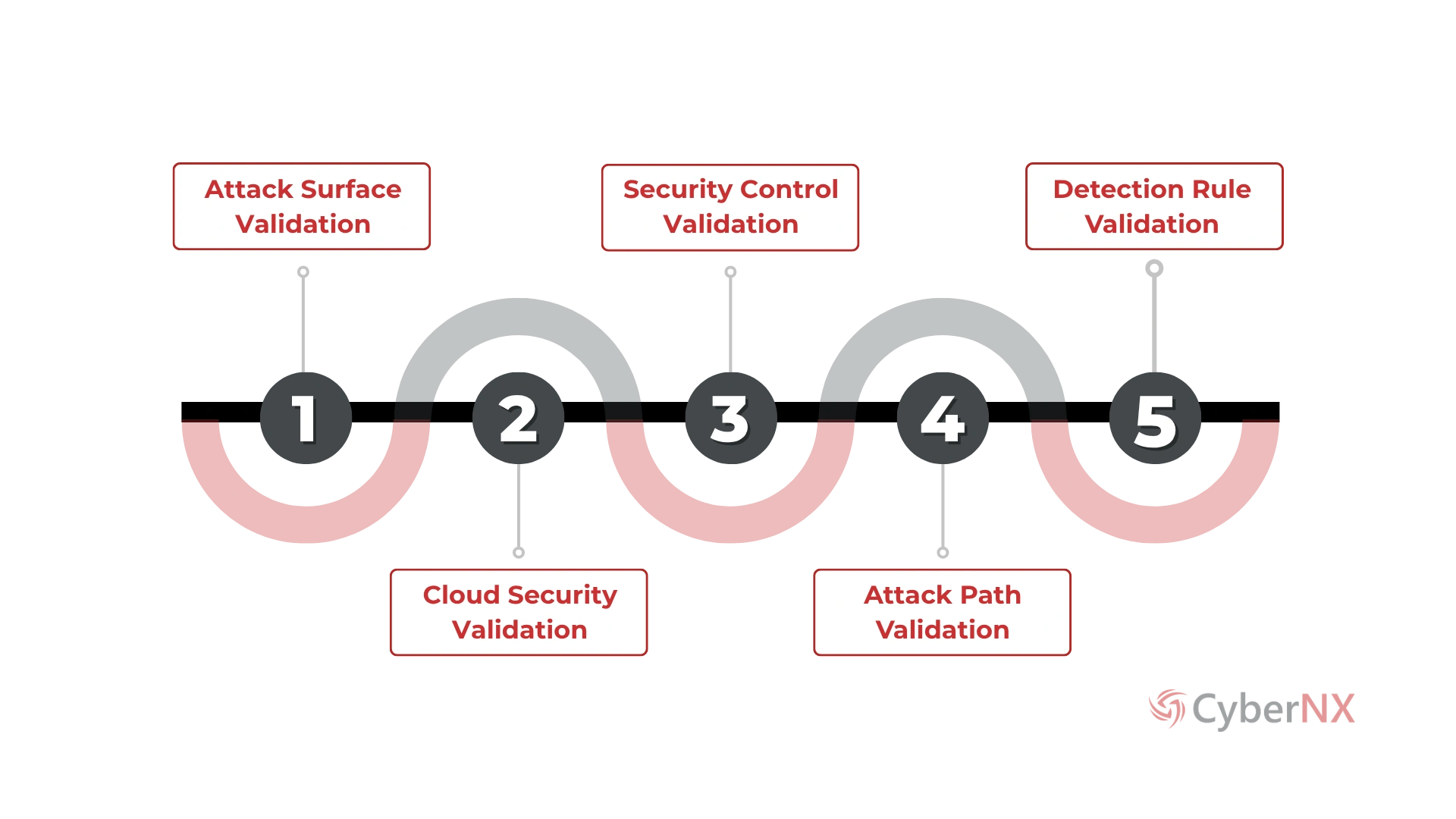
We address your key challenges:
Making sure strong security across a range of cloud and on-premises environments, which often leaves holes and weaknesses in security.
Managing and protecting IT systems that are complicated and always changing, which raises the risk of vulnerabilities that aren’t found.
Ransomware, phishing, and zero-day attacks are examples of advanced cyber threats that can get around normal security measures.
The organization needs to make sure that threat detection is ongoing and working well, and that it can quickly find threats and react to them.
Putting in place strong security means that it doesn’t slow down the system or make the user experience worse.
PROCESS
How It Works?
Contact Us for Comprehensive Breach Attack Simulation Exercise
APPROACH
Why Choose CyberNX for Breach Attack Simulation Services?
01
Initial Consultation
02
Environment Assessment
03
Scenario Development
04
BAS Execution
05
Analysis & Reporting
06
Post-Exercise Consultation
Customer first Approach is our guiding principle.
BENEFITS
Comprehensive Breach Attack Simulation (BAS) Service
Customized Security Insights
Get customized cybersecurity insights through initial consultations that make sure BAS exercises are perfectly in line with the security goals and challenges of your company.
Comprehensive Risk Mitigation
Find and fix vulnerabilities in all areas of IT - servers, endpoints, APIs, cloud environments, and apps, to make sure there is strong protection against a wide range of cyber threats.
Optimized Resource Utilization
The data can be used to fine-tune security tools to make them work better and faster, making your cybersecurity investments more useful.
Proactive Threat Management
Make your monitoring better so you can find new threats quickly and respond to them.
Continuous Improvement
The results and suggestions help organizations make their defense stronger.
For Customized Plans tailored to Your Needs,
Get in Touch Today!
FAQ
Frequently Asked Questions
RESOURCES

