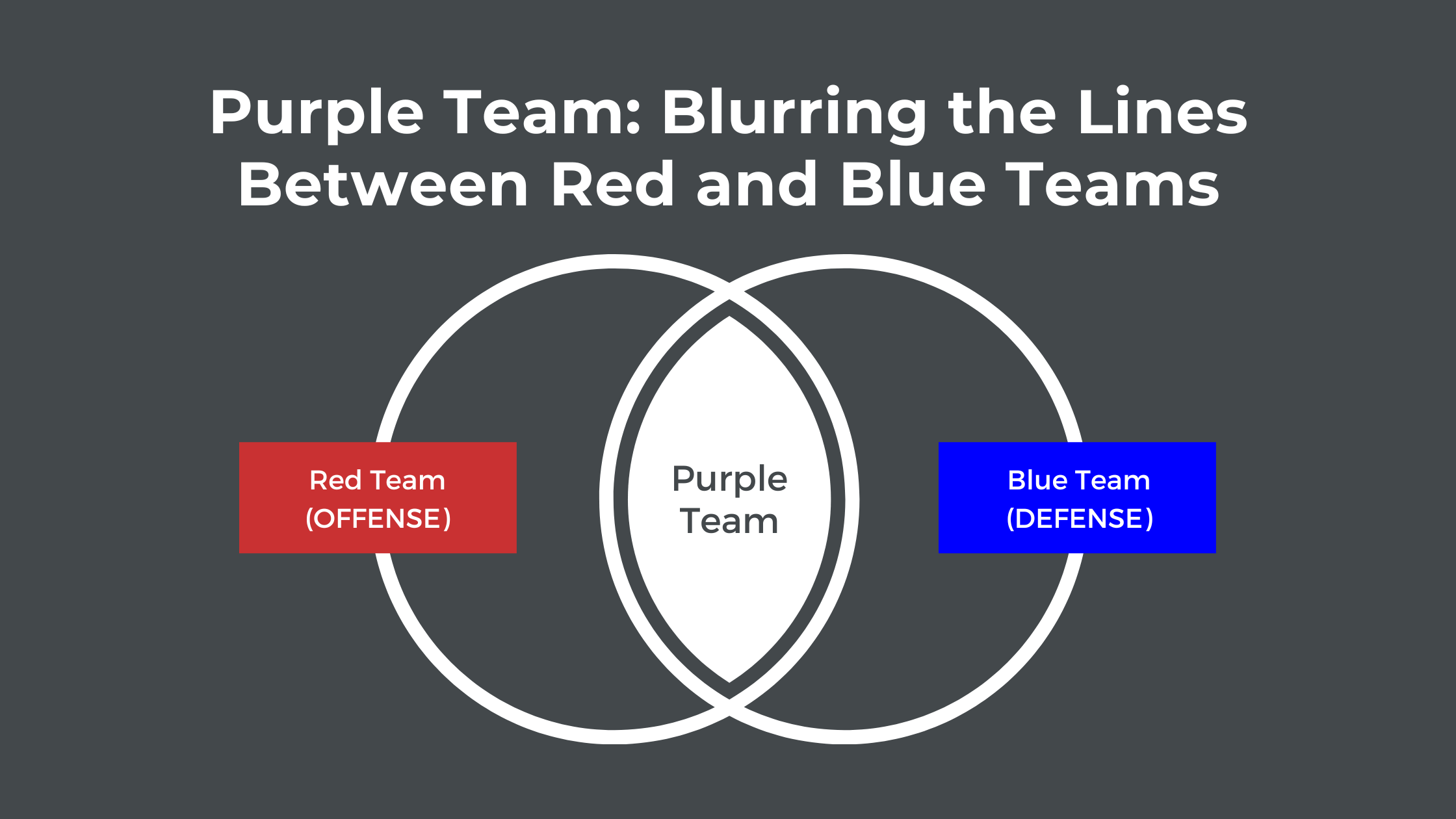
Purple Team Cybersecurity: Enhance Security with Real-Time Collaboration
In the ever-evolving landscape of cybersecurity, CISOs, CXOs, and IT Managers are constantly seeking innovative strategies to fortify their defenses.
Contents
The Securities and Exchange Board of India’s (SEBI) Cybersecurity and Cyber Resilience Framework (CSCRF) is a significant step towards enhancing the cybersecurity landscape for Regulated Entities (REs). This framework emphasizes the importance of managing supply chain risks, and the Software Bill of Materials (SBOM) emerges as a critical tool in this objective.
An SBOM is essentially a comprehensive inventory of software components, akin to a recipe listing its ingredients. It details open-source and third-party components, their versions, patch status, and licensing information. By leveraging SBOMs, security teams can proactively identify and address potential vulnerabilities and licensing issues within their software ecosystem.
The CSCRF mandates REs to obtain SBOMs for their critical systems, both existing and newly procured. This requirement underscores the need for transparency and accountability in the software supply chain.
CyberNX having years of experience in regulatory compliance management can assist REs in achieving SBOM compliance and overall CSCRF adherence. Our services include:
SBOM is a powerful tool for enhancing cybersecurity and mitigating supply chain risks. CyberNX, can help REs can effectively navigate the complexities of CSCRF compliance and safeguard their operations in the digital age. Contact us for comprehensive CSCRF compliance requirements.
A Software Bill of Materials (SBOM) is a comprehensive inventory of all the components, libraries, dependencies, and modules that make up a software application. It provides detailed information about the software supply chain, including version numbers, licenses, and origin of the components. SBOMs are essential for identifying potential vulnerabilities, ensuring compliance with open-source licenses, and maintaining transparency in software development. By adopting SBOM practices, organizations can enhance their cybersecurity posture and manage risks associated with third-party components.
SBOM is crucial for maintaining visibility into the components used in software projects. With modern software relying heavily on third-party and open-source components, it is easy for outdated or vulnerable libraries to slip into production. An SBOM helps developers and organizations track these components, enabling proactive vulnerability management. Additionally, it aids in meeting compliance requirements, ensuring software meets security standards, and streamlining incident response by quickly identifying affected components in case of a vulnerability disclosure.
An SBOM enhances cybersecurity by providing a detailed view of all the components in an application, making it easier to identify and address vulnerabilities. It supports the implementation of secure software development practices by promoting transparency and accountability in the supply chain. Furthermore, in case of a cyberattack or data breach, an SBOM allows rapid identification of the compromised components, facilitating efficient remediation. By incorporating SBOMs into security policies, organizations can reduce the risk of supply chain attacks and ensure their software meets robust security standards.
While SBOMs are valuable, their implementation comes with challenges. Maintaining an up-to-date and accurate SBOM can be resource-intensive, especially in large-scale projects with complex dependencies. Additionally, organizations must ensure compatibility between tools used to generate and manage SBOMs across various development environments. Another challenge is educating teams about the importance of SBOMs and integrating them seamlessly into existing development workflows. Despite these obstacles, the long-term benefits of improved security and compliance make SBOM adoption a worthwhile endeavor.
Share on
RESOURCES

In the ever-evolving landscape of cybersecurity, CISOs, CXOs, and IT Managers are constantly seeking innovative strategies to fortify their defenses.
In the relentless battle against cyber threats, CISOs, CXOs, and IT Managers are constantly seeking ways to fortify their organization’s

Cybersecurity is a continuous battle, not a one-time fix. In today’s complex digital world, threats are constantly evolving, becoming more
RESOURCES
Cyber Security Knowledge Hub