Many organisations today face a dilemma. They know that around-the-clock monitoring, rapid incident response, and proactive threat detection are critical to protecting their business. Yet, the idea of building and maintaining a full-scale Security Operations Centre (SOC) – with the right people, tools, and processes – often feels daunting. And sometimes, expense and complexity make security leaders reluctant.
That’s where SOC as a Service (SOCaaS) changes the game. It combines advanced technology with expert human intelligence and delivers enterprise-grade security monitoring and response. And your organisation can opt for it without the burden of running it all in-house.
In this blog, we’ll unpack what everything you should know about SOC as a Service. The key focus areas would be – how SOCaaS operates in real-world scenarios and how to determine if this model fits your organisation’s security needs.
First: What is SOC as a Service?
SOC as a Service (SOCaaS) is a third-party, subscription-based security offering that covers monitoring, detection, response and remediation of cyber-threats. In contrast to a traditional in-house SOC which you build, staff and run yourself, SOC as a Service shifts those responsibilities to a provider.
Because the provider delivers 24/7 monitoring, advanced analytics, threat intelligence and incident handling, it allows organisations to “buy” security operations rather than “build” them from scratch.
This model becomes especially relevant for organisations with limited budgets or teams. Plus, it is also appealing to larger enterprises looking for flexibility and speed.
Why adopt SOC as a Service?
Organisations turn to SOC as a Service for several clear benefits:
1. Cost-effectiveness
Building an internal SOC is a heavy lift. You need infrastructure, tools, staffing, training and maintenance. With a managed SOC as a service, you avoid many of the upfront costs and ongoing maintenance burdens. Moreover, the subscription pricing model brings predictability to your security budget.
2. Access to specialist expertise
Security operations teams are in high demand. Finding and retaining skilled analysts, threat hunters and responders is difficult and expensive. A managed SOC as a Service provider already has this talent and can bring it to your organisation. This also means you benefit from threat-intelligence aggregation across many clients, seeing patterns you alone might not.
3. Faster time to value and scalability
Because the service model leverages existing infrastructure and processes, you can ramp up more quickly than building in-house. You also gain the flexibility to scale up (or down) as your business or threat landscape changes. This agility is increasingly valuable in a fast-moving threat environment.
4. 24/7 coverage and modern tooling
Many organisations struggle to maintain round-the-clock monitoring. Managed SOC as a Service providers do that by default. They also bring tools like SIEM, UEBA, SOAR, behavioural analytics and advanced threat intelligence as part of the service. Together these capabilities bolster your maturity without requiring you to master everything internally.
What problems does SOC as a Service solve
Many organisations face the following challenges:
- A shortage of skilled analysts and high staff turnover.
- Monitoring tools generate many alerts – but few get triaged into meaningful action.
- Visibility gaps across on-premises, cloud and remote endpoints leave blind-spots.
- Compliance and reporting demands that stretch resources.
- Legacy security operations that are reactive, fragmented or fragmented across business units.
By partnering with a managed SOC service you:
- Fill the analytic and operational gaps.
- Get unified coverage across multiple environments and cloud/on-prem.
- Shift part of the burden from your team to the provider, enabling your team to focus on higher-value tasks.
- Leverage proven processes and tools to reduce risk and improve responsiveness.
As one domain leader summarises: “SOC as a Service is especially useful for organisations that do not have the resources or expertise to run a full-scale, in-house SOC.”
How SOC as a Service works
When you engage a SOC as a service provider, the journey broadly follows these phases:
1. On-boarding & integration
The provider begins by integrating your log sources, endpoints, cloud infrastructure, network devices, identity systems, and applications into their monitoring framework. This phase often involves configuring agents, adjusting log flows, setting thresholds and defining custom alert rules.
You will also collaborate on defining your risk profile, critical assets, escalation channels and service-levels.
2. Monitoring, detection and triage
Once live, the provider monitors your environment 24/7. They collect events from across the estate (network, endpoints, cloud, SaaS apps), apply behavioural analytics, threat intelligence, correlation, automated alerting and prioritisation.
High-priority alerts are triaged by experienced analysts. The provider filters out false positives and escalates real incidents.
3. Response and remediation
For escalated incidents, the provider acts to investigate, contain, remediate or hand-off to your team, depending on contractual scope. They may isolate endpoints, remove malicious files, coordinate with your internal incident response team, and support forensic or root-cause activities.
In many models, you retain strategic control; the provider executes the operational aspects – but you collaborate closely.
4. Reporting and continuous improvement
The service provider delivers regular dashboards, incident reports, trend analysis, and recommendations. These help you demonstrate to stakeholders how security operations contribute to risk reduction and business resilience.
They also support process optimisation, tool tuning, threat-hunting campaigns, and improvements in detection and response capabilities over time.
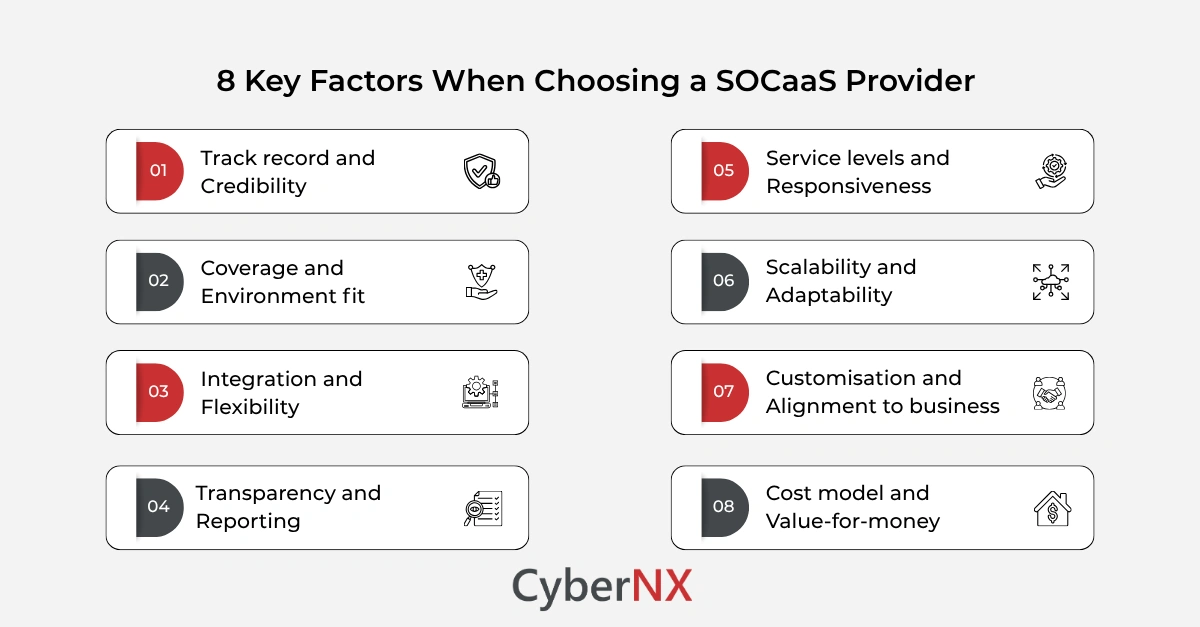
What to look for in a SOC as a Service partner
Selecting the right provider is critical. Consider the following criteria:
- Track record and credibility: Does the provider have experience, references and visible outcomes with organisations of your size or industry?
- Coverage and environment fit: Ensure the service monitors your full estate – on-prem, cloud, SaaS, remote endpoints, OT if needed.
- Integration and flexibility: Will the provider integrate smoothly with your existing tools (EDR, IAM, cloud logs, SIEM, etc) and workflows?
- Transparency and reporting: Are SLAs clear? Are dashboards meaningful? Do you get actionable insights, not just alerts?
- Service levels and responsiveness: What is the mean time to detect (MTTD) and respond (MTTR)? Are escalation paths defined?
- Scalability and adaptability: Can the service scale as you grow or as new threats emerge?
- Customisation and alignment to business: Does the provider align to your risk profile, industry regulations and strategic goals?
- Cost model and value-for-money: Does the pricing align with your budget, and does it deliver measurable security improvements?
How effective SOC as a Service delivers value
When done well, managed SOC as a Service becomes a strategic asset – not simply a check-box project. Some of the key value drivers include:
1. Improved visibility and risk prioritisation
You gain a unified view of your digital assets, threat vectors, and security posture. This visibility enables you to prioritise risk based on business impact, not just volume of alerts.
2. Faster detection and response
With dedicated monitoring and triage capabilities you shrink time to detect and respond, reducing dwell time and limiting damage.
3. Enhanced operational resilience
With a mature SOC service, you can reduce downtime, data loss and regulatory costs. You build trust with customers, partners and regulators.
4. Scalability with growth
As your business scales or enters new markets, your SOC service scales too. You don’t need to rebuild or re-staff the internal team from scratch.
5. Focus on strategic security
With the operational burden outsourced, your internal security team can focus on strategy: risk management, architecture, compliance, governance and business alignment.
6. Cost-effectiveness and predictability
The subscription-model converts unpredictable incident and staffing cost into a predictable line item. You can budget security more clearly and compare service value year on year.
Trends shaping SOC as a Service
SOC as a Service is evolving quickly. Here are some of the key trends:
- AI and machine learning augmentation: Providers are increasingly using AI/ML to triage alerts, prioritise threats and even automate certain response actions. This helps manage alert overload and analyst fatigue.
- Cloud-native SOC models: With more workloads shifting to cloud and hybrid architectures, SOCaaS services are adapting to provide visibility across containers, serverless, SaaS apps, and multi-cloud environments.
- Hybrid internal/external models: Many organisations adopt a “co-managed” model: your internal team handles strategy and escalation, while the managed SOC as a Service provider handles operations. This hybrid approach combines control and expertise.
- Threat hunting and proactive operations: Instead of only reacting, modern SOC as a Service providers offer threat-hunting, intelligence-driven investigation and advanced analytics.
- Security as a business enabler: The providers are expected to speak the language of business risk, compliance and growth – not just “alerts per hour”. Reporting emphasises outcomes such as reduced downtime, improved customer trust, regulatory readiness and faster time-to-remediation.
- Edge and OT coverage: As operational technologies, IoT and remote sites become more integrated, SOC services are extending into these domains for 24/7 monitoring outside the core enterprise network.
Common mistakes and how to avoid them
Even though SOC as a Service offers many advantages, decision-makers need to watch common traps.
- Mis-aligned scope: If you don’t clearly define your assets, environments, threat landscape and objectives, you may engage a provider whose scope does not cover your full risk surface. Clarify scope from day one.
- Poor onboarding and configuration: The initial integration can be complex – log sources may be missing, cloud workloads overlooked, agents mis-configured. Ensure that both parties allocate time and resources for onboarding.
- Over-reliance without internal ownership: Outsourcing operations doesn’t mean you abdicate strategy or governance. Your team still needs to oversee the service, define risk priorities and integrate outputs into broader governance.
- Ignoring customisation: A generic service may not align with your particular industry or regulatory demands. Demand that detection rules, escalation workflows and reporting map to your context.
- Lack of measurement: Without tracking MTTD, MTTR, false-positive rates and other KPIs, you can’t judge service value. Set measurable metrics early and review them periodically.
- Vendor lock-in risk: Ensure you retain visibility of raw logs, rule sets and have an exit plan. A provider that holds everything in a black box creates future risk.
- Neglecting human factors: Automation is great, but the human analyst remains key. Make sure your provider uses skilled analysts and provides continuous improvement of their team and tools.
Conclusion
SOC as a Service provides a practical, efficient route for organisations to enhance their security posture without the massive lift of building and running a full internal SOC. It brings expert people, proven processes and modern technology under a subscription model. As you evaluate options, keep your business goals, risk profile and operational realities front-of-mind.
At CyberNX we believe SOC as a Service is not about off-loading responsibility; it is about empowering your business with an operational security edge. We can partner with you to help assess your needs, choose the right SOC-as-a-service model and integrate it into your broader security ecosystem. Every step you take strengthens your resilience.
Reach out to us to explore how SOC as a Service can be a game-changer for your organisation.
SOC as a Service FAQs
What is the difference between SOC as a Service and a traditional in-house SOC?
A traditional SOC is built and operated internally by the organisation. It requires infrastructure, staffing, tools and ongoing investment. SOC as a Service is outsourced, subscription-based, and leverages provider expertise and infrastructure.
Can small or mid-sized organisations benefit from SOC as a Service?
Yes. SOCaaS is especially useful for organisations that lack the resources or expertise to build a full internal SOC. It lets them “buy” operational security at enterprise scale.
Will a SOC as a Service provider replace my internal security team entirely?
Not necessarily. Many organisations adopt a hybrid or co-managed approach. The provider handles operations while your team retains strategic oversight, governance, architecture and risk-management.
How much does SOC as a Service cost and how do we budget for it?
Costs vary widely by scope, assets, environment, service-levels and number of endpoints. The subscription model makes budgeting more predictable than building in-house, but you should request clear pricing tiers, SLAs and value metrics.